The Lazarus Group – North Korea elite hacker organizations – appears to have stepped up its operations recently, carrying out four confirmed attacks on crypto entities since June 3.
They are now suspected of carrying out a fifth attack, this time targeting the CoinEx crypto exchange on September 12. In response, the company announced a few tweets indicating that suspicious wallet addresses are still being identified, therefore the total value of the stolen funds is not yet known, but is currently believed to be around $54 million.
In the past 104 days, Lazarus has already been identified as responsible for stealing nearly $240 million in cryptoassets from Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), and Stake .com ($41 million).
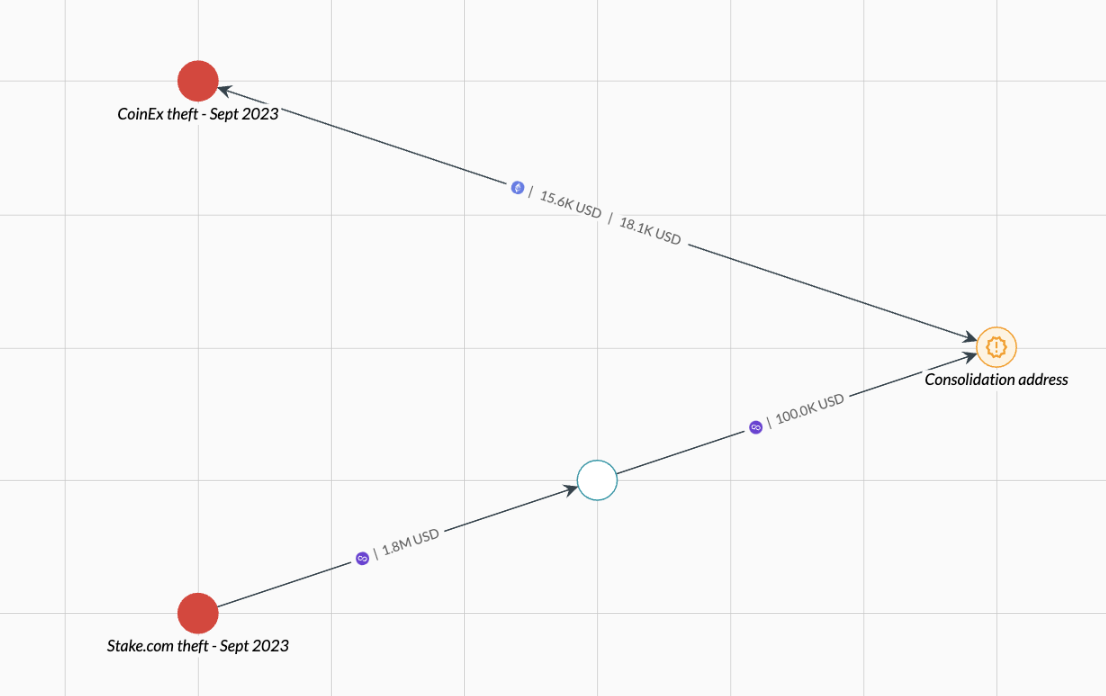
As seen in the table above, Elliptic’s analysis confirms that some of the funds stolen from CoinEx were sent to an address used by the Lazarus group to launder the funds stolen from Stake.com, albeit on a different blockchain. The funds were then transferred to Ethereum, using a bridge previously used by Lazarus, and then returned to an address known to be controlled by the CoinEx hacker.
Elliptic noticed this commingling of funds from separate hacks before Lazarus, the last time crypto stolen from Stake.com overlapped with funds stolen from Atomic Wallet. These cases where funds from different hacks were consolidated are shown in the graph below in orange.
In light of this blockchain activity, and in the absence of information suggesting that the CoinEx hack was carried out by any other threat group, Elliptic agrees that the Lazarus Group should be suspected of stealing funds from CoinEx.
Five Lazarus attacks in 104 days
In 2022, Lazarus was credited with several high-profile hacks, including Harmony’s Horizon Bridgeand Axie Infinity’s Ronin Bridge, and both happened in the first half of last year. From then until June of this year, no major crypto heists were publicly attributed to Lazarus. As a result, the various hacks over the past 104 days represent a step further in activity for the North Korean threat.
- June 3, 2023 Atomic Wallet users – a decentralized custody-free cryptocurrency wallet – lost over 100 million dollars. Elliptic attributed this hack to Lazarus June 6, 2023, after multiple factors were identified to indicate that the North Korean threat group was responsible. This attribution is later confirmed by the FBI.
- On July 22, 2023, Lazarus gained access to hot wallets belonging to the CoinsPaid crypto payment platform through a successful social engineering attack. This approach allowed attackers to create authorized requests to withdraw approximately $37.3 million in crypto assets from the platform’s hot wallets. July 26, CoinsPaid published the report claiming that Lazar was responsible for this attack. This attribution is later confirmed by the Federal Bureau of Investigation (FBI).
- On the same day, July 22, Lazarus launched another high-profile attack, this time against centralized crypto payment provider Alphapo, stealing $60 million in crypto assets. Attackers may have gained access via previously compromised private keys. As stated above, The FBI later attributed this attack to Lazarus.
- On September 4, 2023, online crypto casino Stake.com suffered an attack in which approximately $41 million in virtual currency was stolen, possibly as a result of a stolen private key. The The FBI issued a press release on September 6, confirming that the Lazarus group was behind this attack.
- Finally, on September 12, 2023, the centralized crypto exchange CoinEx was the victim of a hack, in which $54 million was stolen. As noted above, a number of factors point to Lazar being responsible for this attack.
A change of tactics?
An analysis of Lazarus’ recent activity suggests that since last year it has shifted its focus from decentralized to centralized services. Four of the five recent hacks we discussed earlier involved centralized Virtual Asset Service Providers (VASPs). Centralized exchanges were previously Lazarus’ goal before 2020, before the rapid rise of the decentralized finance (DeFi) ecosystem.
There are a number of possible explanations as to why Lazarus’ attention may have returned to centralized services.
Increased focus on security
Elliptic’s previous research on DeFi hacks In 2022, they found that one exploit occurred every four days, with each theft averaging $32.6 million.
Cross chain bridges – which were a relatively new form of service in early 2022 – are becoming some of the most commonly hacked types of DeFi protocols. These trends have likely led to improvements in smart contract auditing and development standards, reducing the space for hackers to identify and exploit vulnerabilities.
Susceptibility to social engineering
For many of its hacks, Lazarus Group’s attack methodology of choice is social engineering. The $540 million Ronin Bridge hack, for example, was credited to a fake job offer on LinkedIn.
However, decentralized services often boast a small workforce and – as the name suggests – are decentralized to varying degrees. Therefore, gaining malicious access to the developer does not necessarily equate to gaining administrative access to the smart contract.
Centralized exchanges, meanwhile, are likely to have a larger workforce, expanding the range of possible targets. They are also likely to operate using centralized internal IT systems, allowing Lazarus malware a greater chance to penetrate the intended functions of their business.
Elliptic will continue to monitor these incidents and update our system with new information about stolen funds.
Featured Crypto Crime Global



