[Updated: 28 July] On July 15, Twitter suffered a major breach, allowing hackers to post fake tweets across 130 compromised accounts owned by a number of high-profile individuals and corporations.
Using a common fraud technique known as “gift fraud”, these accounts were used to defraud around 400 victims out of a total $121,000 in Bitcoin.
The addresses used were part of a larger wallet, which previously received about $65,000 in bitcoins between May and July 2020. New York Times registered that some of these funds may have come from the sale of stolen twitter accounts.
At the end of last week this wallet was emptied. Thanks to the transparency of the bitcoin blockchain, along with Elliptic’s analytical capabilities and rich data set of crypto addresses, we can track the money and see where those bitcoins were sent.
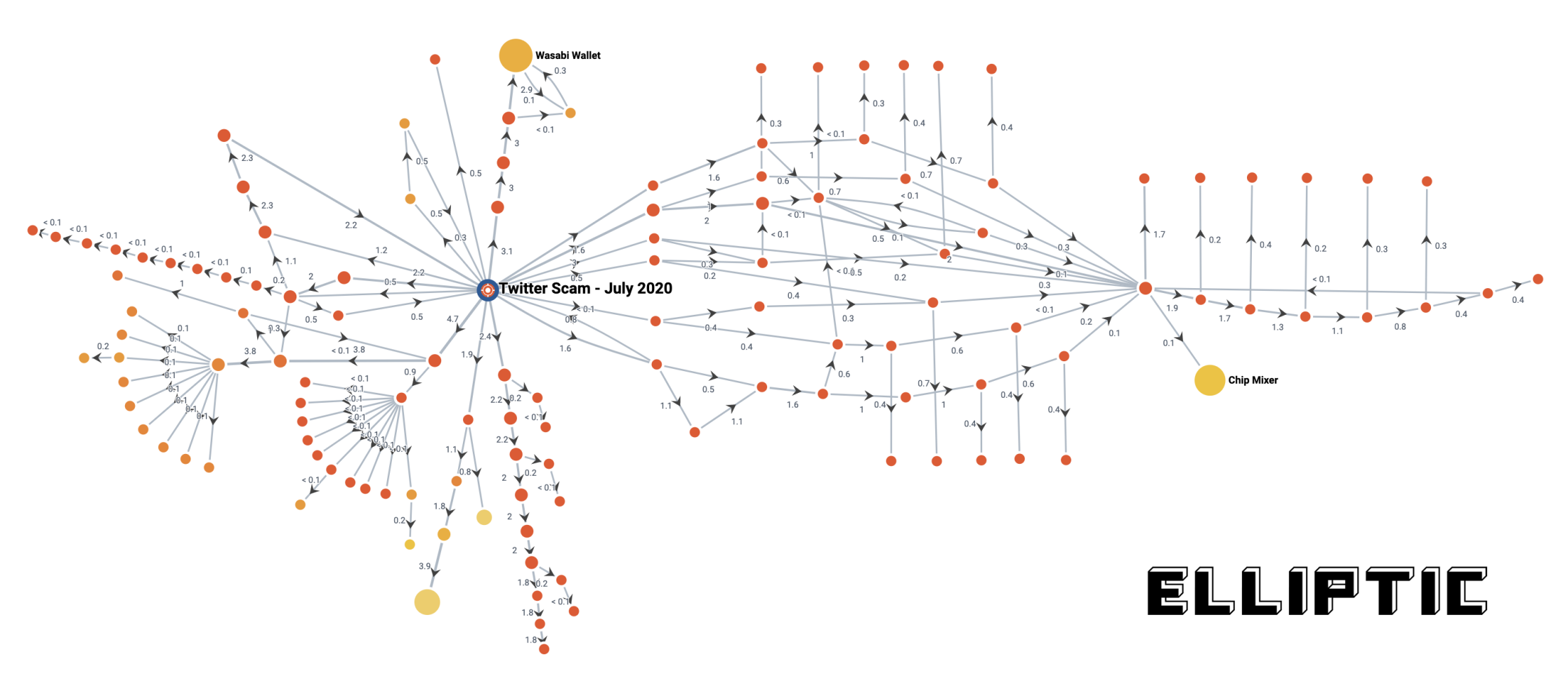
The diagram above shows a simplified representation of the flow of bitcoins from a hacked wallet, taken from Elliptic Forensics – our crypto asset research software. Not all transaction and wallet links are shown for simplicity. Each circle is a bitcoin wallet and the lines show the flow of funds between them. What is clear is that the funds were split into smaller amounts and passed through many new wallets. This is a tactic commonly used by those seeking to launder the proceeds of crime: splitting and combining funds with other more legitimate bitcoins to hide the connection to their illicit source.
On the left side of the diagram, you can see two parts of funds that are divided into several smaller packages of exactly the same amount, all of which are held on newly created bitcoin addresses. There are indications that these addresses may be part of a mixing service.
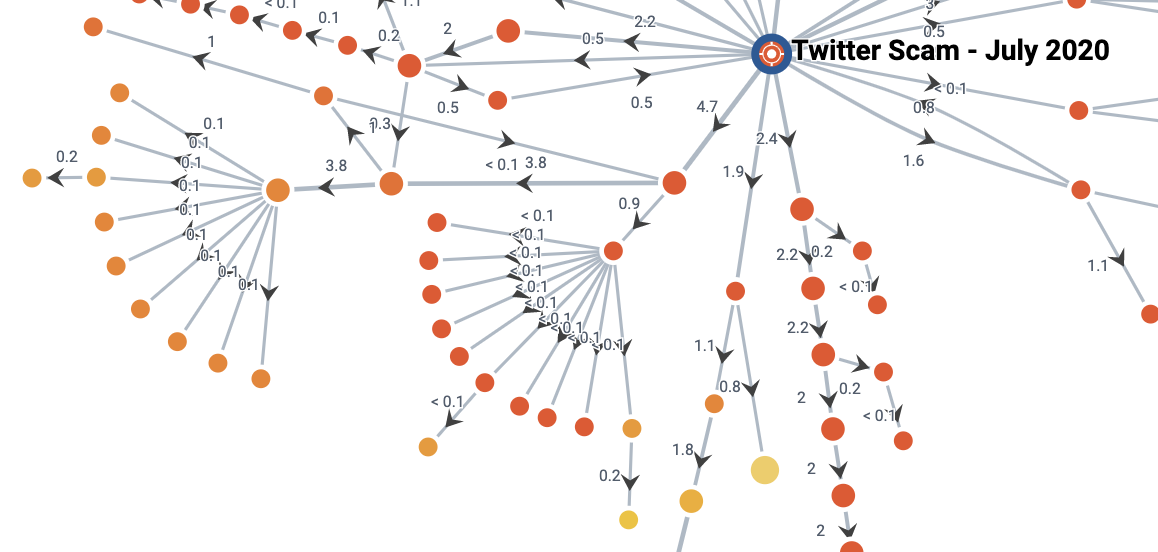
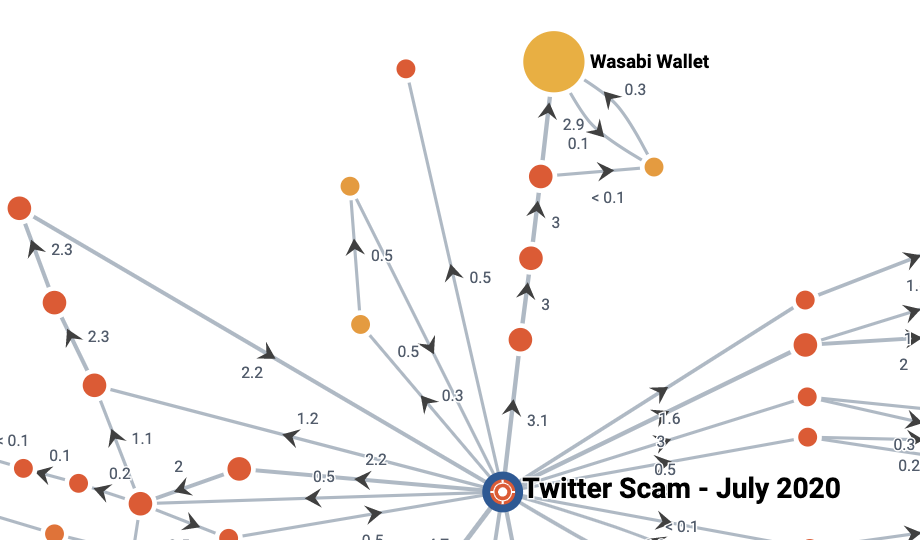
We can safely say that at least 15% of bitcoins are mixed, using ChipMixer and Wasabi Wallet services. Bitcoin mixers combine funds from different sources, making it difficult if not impossible to trace the bitcoins further – this is another common technique used by those who launder the proceeds of crime in bitcoins.
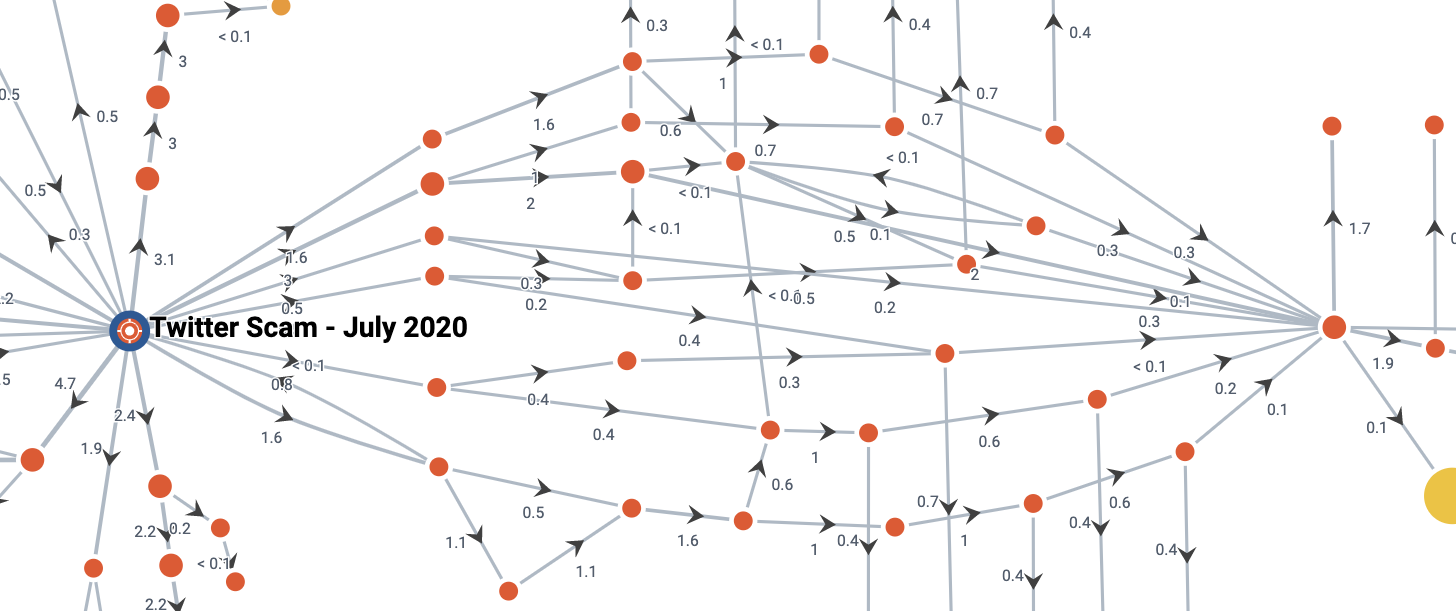
Our chart does not show (for confidentiality reasons) the flow of funds to various businesses, including currency exchanges, gambling services and merchant service providers (which suggests that goods or services are purchased by some of the funds). The amounts spent in this way are small and make up a few percent of the funds. However, these connections to regulated businesses will be the primary line of inquiry for law enforcement investigators, who will be able to seek details of the accounts that received these transactions.
One thing to keep in mind is that as these funds move between wallets, they may no longer be under the control of the hacker. They may have sold or spent their bitcoins outside of a recognized service such as an exchange. However, the structure of the transaction graph gives us some clues about this. For example, on the right side of the diagram we see several outflows totaling 8.1 bitcoins. Much of this is then split into new addresses, but much of it is consolidated back into a single wallet – indicating that these separate streams were actually controlled by the same person.
The washing process has just begun. Our analysis shows that various techniques have already been used to help break the link to the Twitter hack – from using mixers, to splitting funds into smaller amounts across multiple transactions. However, it appears that most of the funds from the hacked wallet have yet to be spent or cashed out via an exchange. Those in control of the funds bide their time and figure out how to pay out the money without identification, even as the world watches on the blockchain.
The situation is changing rapidly, and we will continue to inform you of the latest developments.
You can follow our live updates at Twitter and LinkedIn.
Related Articles:
- Insights from Elliptic: #Twitterhack and Bitcoin Money Laundering
- Elliptic Identifies Probable Use of Wasabi Wallet Service to Launder Twitter Hack Bitcoins
- Over 50% of #TwitterHack bitcoins now sent via mixer – What does this mean for crypto AML?
Don’t already have an Elliptic backup of your crypto AML compliance operations?

Financial services in accordance with regulations



