What actually happens during a ransomware attack? We follow a real case involving the REvil ransomware – from initial infection and negotiations, to cryptocurrency payments and money laundering.
Ransomware attacks continue to grow in volume and severity. Cybercriminal groups like DarkSide have received hundreds of millions of dollars in cryptocurrency ransom payments, crippling critical infrastructure providers such as Colonial Pipeline. In early July, hundreds of businesses were infected with REvil ransomware (also known as Sodinokibi), through an attack on Kaseya – a supplier of IT software for managing these victims.
At Elliptic, we track and investigate ransomware groups to gather information about the cryptocurrency wallets they use to receive ransoms. These insights are then available in our softwareenabling law enforcement to track the money and potentially freeze the funds or identify the people behind the attacks. Cryptocurrency exchanges and financial institutions use our software verify client deposits to link to these wallets and ensure that ransomware groups cannot cash out their revenue.
This research gives us a unique insight into the entire life cycle of a ransomware attack – from the initial malware infection and ransom demand, through the negotiation and payment process, and finally the laundering of funds. In this article, we track one specific attack by the Russia-linked REvil ransomware group that has occurred over the past few weeks. Some images have been edited to protect the victim’s identity.
1. The victim is infected with REvil malware
Once the REvil malware makes its way onto a computer system, it encrypts the victim’s files – leaving behind a text file containing a ransom message, shown below:
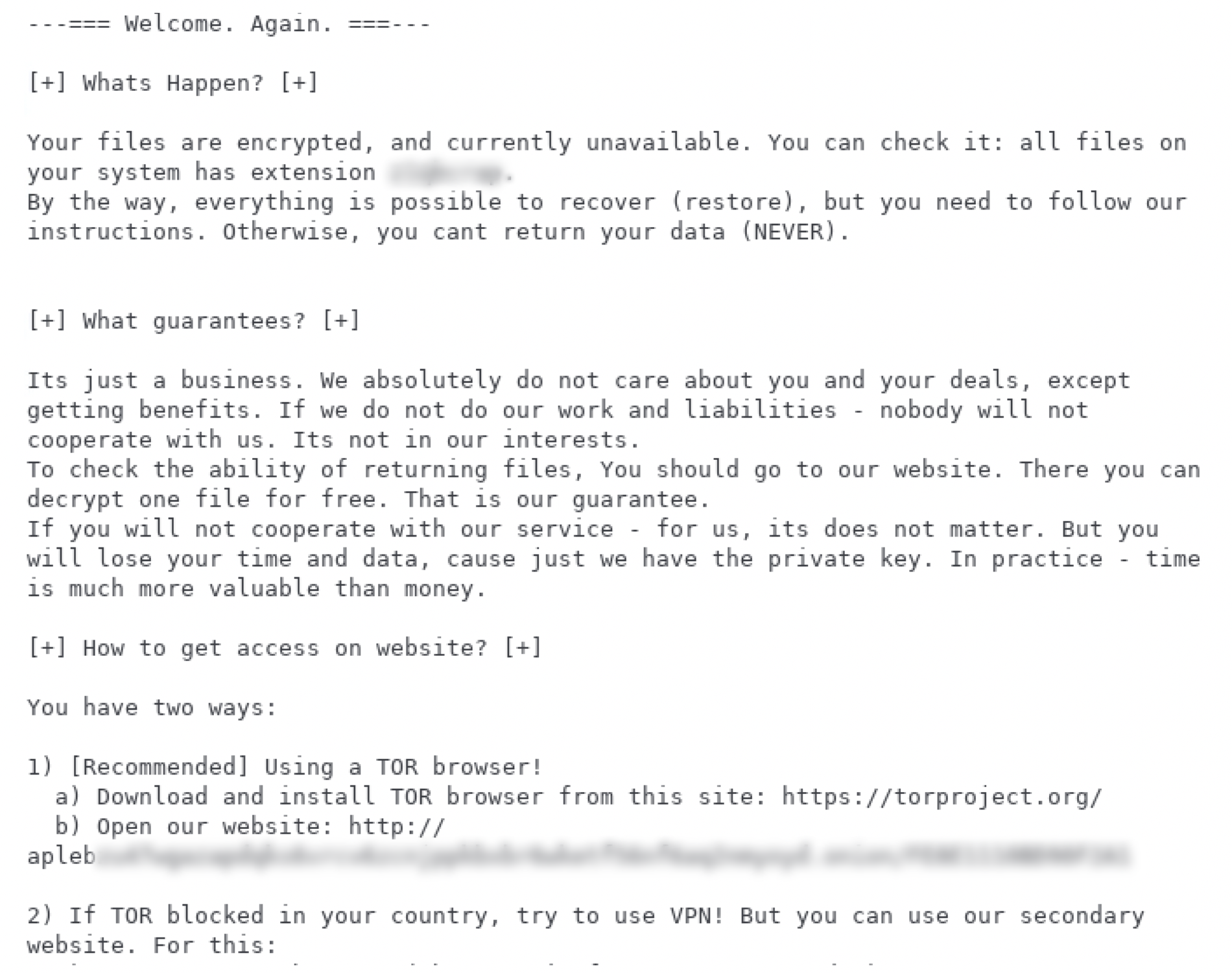
The note directs the victim to a website (the “victim portal”) on Tor (an anonymous version of the Internet often used to host darknet markets), to access further instructions.
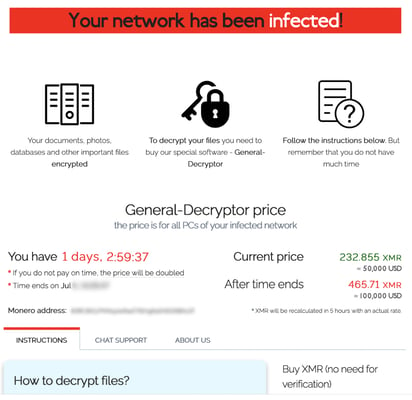
2. Access to the victim’s portal
The victim portal displays a ransom demand – $50,000 in Monero, a privacy-focused cryptocurrency that is very difficult to trace. If the ransom is not paid within the specified time frame, the ransom will be doubled to $100,000.
The portal provides instructions on where Monero can be bought and exactly where it should be sent:
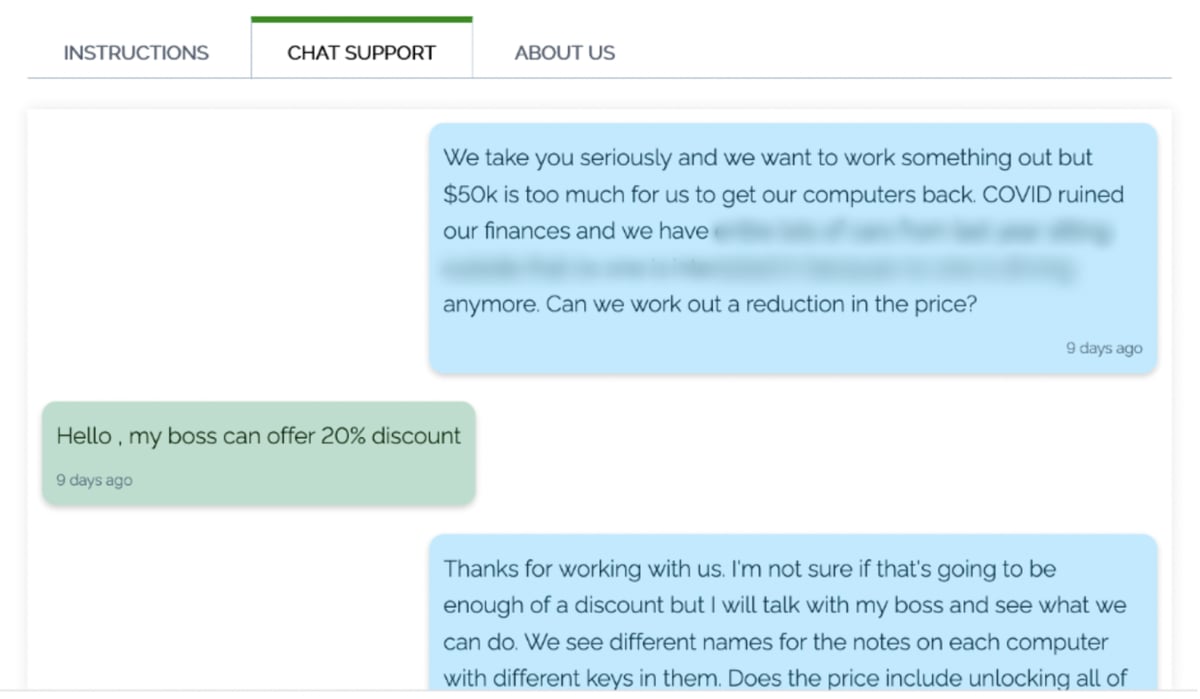
3. Chat support
Similar to an e-commerce site, the portal allows the victim to talk directly with REvil, via a “Chat Support” tab. Here we see the victim (blue) start a conversation with REvilla (green) and start negotiating a ransom:
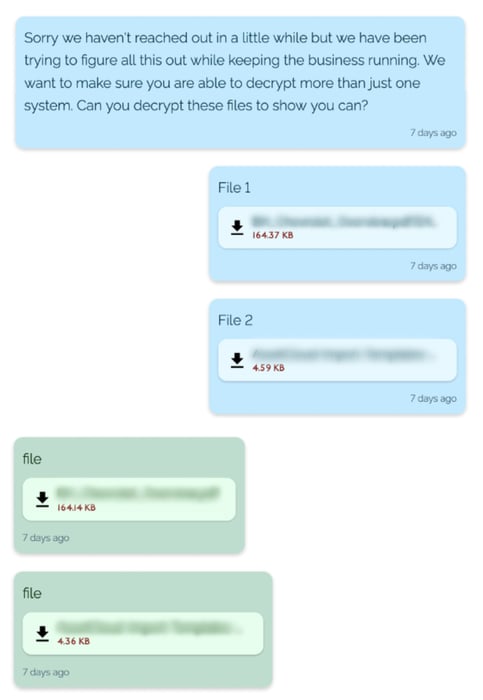
4. Verifying that paying the ransom will lead to decryption
The victim then asks for proof that the payment of the ransom will succeed – ie. that their files will be decrypted. They upload two of their encrypted files, and REvil responds with proof – decrypted files:
5. Payment request in Bitcoin instead of Monero
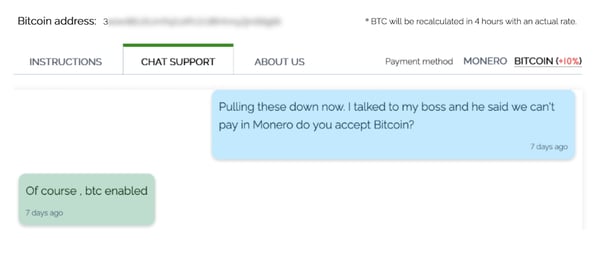
Many ransomware victims find it difficult to obtain the Monero needed to pay the ransom (it is not listed by many exchanges, especially in the US), or they do not want to pay in Monero due to concerns about violating sanctions. Most ransomware response companies that negotiate and pay on behalf of victims simply refuse to pay the Monero ransom.
In this case the victim asked to pay in bitcoins instead and REvil allowed it, albeit with a 10% surcharge. This higher amount reflects the increased risk REvil faces when accepting Bitcoin payments, due to its traceability. The portal updates to display the Bitcoin payment address:
6. Negotiating the ransom amount
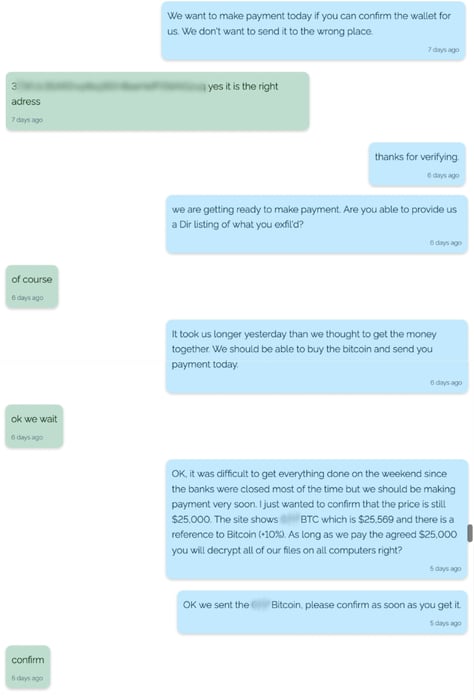
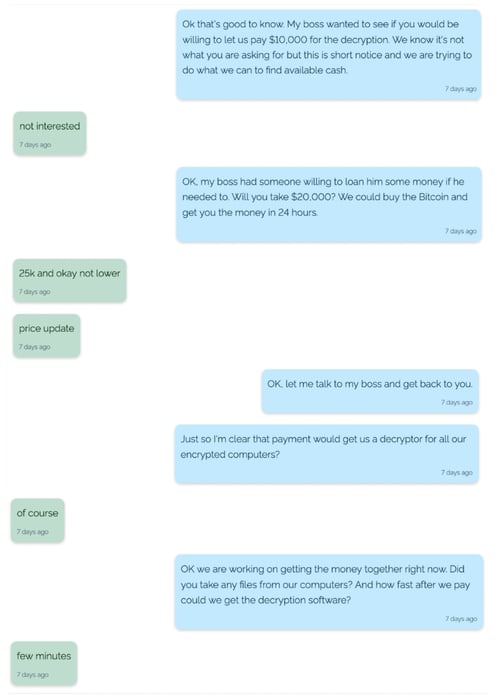
Having already negotiated a 20% discount on the initial ransom demand of $50,000, the victim goes further – offering only $10,000. They claim that this is all they can pay on such short notice, but REvil rejects the offer. The victim then says that they may be able to borrow some additional money and eventually agree to pay the $25,000 ransom.
7. Sending Bitcoin Ransom
The address to which the bitcoin ransom should be sent is displayed at the top of the portal, but the victim asks REvil to confirm that it is correct. Cryptocurrency payments are irreversible, so it is important to verify the destination address before the transaction.
Victim sends $25,000 in Bitcoin and REvil confirms receipt:
8. A decryption tool is provided
After the ransom is paid, the victim’s portal is updated to allow access to decryption. (Of course, in general, there is no guarantee that such a tool will be provided.)
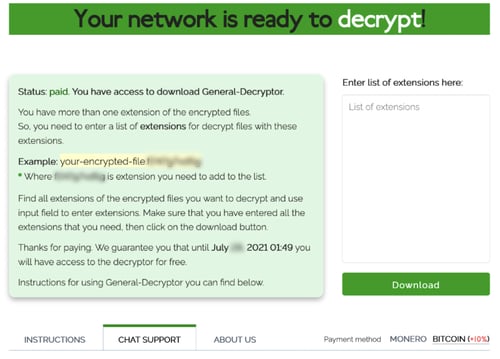
For the victim, the process is now over. They can use a decryption tool to regain access to their files and continue working.
9. Bitcoin is laundered
For REvil, the next step is to launder and cash the Bitcoin ransom. The image below is from our cryptocurrency research software, Elliptic Forensicswhich shows the destination of the Bitcoin ransom paid by this particular victim. Most exchanges that allow the conversion of Bitcoin to traditional currency use Elliptic’s tools to track customer deposits and ensure that they are not linked to illicit activities like this.
REvil must therefore attempt to launder the funds and trace the transaction. They try to do this by “layering” the funds – splitting them up and passing them through many different wallets, and mixing them with bitcoins from other sources. This laundering process in this case is still ongoing, but still, we can already trace part of the funds to the exchanges. Those exchanges will have information about the identities of the people whose accounts received the funds – providing strong leads for law enforcement.

The victim in this case appears to have been a small business rather than a large corporation – as reflected in the relatively small ransom demanded. Small businesses do 50-75% of all ransomware victimsand the impact of these attacks can be catastrophic.
At Elliptic, we believe that ransomware can be combated by limiting the extent to which the criminals responsible can profit from their crimes. By mapping and understanding cryptocurrency flows from ransomware wallets, we can help law enforcement and financial institutions identify perpetrators and freeze their funds.
Join our upcoming webinar on July 29: Tracking Ransomware with Blockchain Analytics, as we discuss how and why ransomware uses cryptocurrencies and show how it can be countered using blockchain analytics – including ‘tracking the money’ from cyber criminals’ wallets.
Crypto Crime Regulatory Compliance