About the cyber attack
Around 19:00 UTC on Wednesday, July 15, 2020, a number of Twitter accounts belonging to prominent companies and celebrities were compromised and used for fraudulent crypto-asset fundraising.
Under the guise of COVID-19 generosity, Twitter posts encouraged unsuspecting readers to deposit BTC to receive double the amount in return.
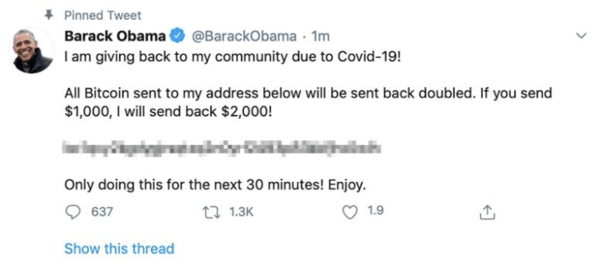
In what is already being described as the most widespread cyber attack to affect the social media platform, over 50 high-profile accounts – belonging to individuals such as Elon Musk and Barack Obama, as well as corporations such as Apple and Uber – have been compromised. By targeting and taking control of these accounts, scammers were able to reach hundreds of millions of followers with their messages.
Although the tweets were quickly deleted, the hackers maintained control of the platform and continued to tweet until Twitter temporarily disabled those accounts with blue ticks to contain the situation.
The crypto side of things
Crypto scams are common and well researched and documented by the Elliptic teambut rarely has such a hoax managed to reach such a wide audience.
In a clear attempt to maximize the financial gain from the attack, the hackers decided to demand payments in bitcoins – the most widely used and accessible cryptocurrency. Some tweets also requested payments in Ripple (XRP), but none were received.
At first, mostly Twitter accounts of crypto exchanges were compromised, and the payouts started coming in. However, payments accelerated when the accounts of more mainstream individuals and businesses, such as Bill Gates and Apple, were included.
Victims
In total, the bitcoin addresses set up by the compromised twitter accounts received just over 400 payments, totaling $121,000.
Given the high-profile nature of this incident, this seems like a relatively small catch. There are similarities to the WannaCry ransomware attack, where a very powerful software exploit was used, but the way it was monetized was relatively unsophisticated, with only $107,000 raised. The result achieved here could lead hackers to consider using crypto scams as a means to monetize exploits of this type.
But who were the victims? Using Elliptic’s tracking capabilities, we can determine where these funds came from and where the victims may be located.
The chart below shows the geographic headquarters of the service (usually an exchange), where bitcoin payments to scam addresses originate. Many exchanges operate outside their home country, but it provides some insight into where victims are located.
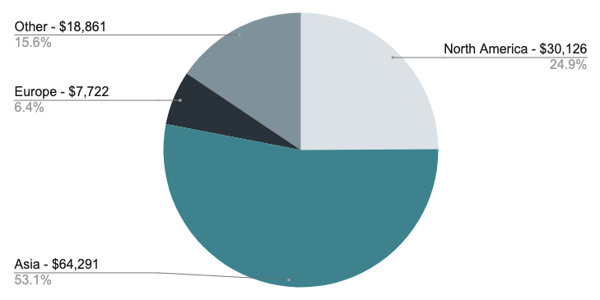
The location of the services from which the fraud originates
Payments from exchanges based in Asia dominate, although this includes one very large payment from an exchange based in Japan, worth $42,000.
Other large contributions come from victims who are likely in North America – not surprising given the affected Twitter accounts.
After bitcoin – the washing began
The hacker has already started moving the bitcoins received to three addresses.
The image below shows a screenshot from Elliptic Forensics, our bitcoin research software. It shows bitcoin flowing from three addresses to other bitcoin wallets. What we see is that almost all the funds have been sent to 12 new addresses, where they are currently located.
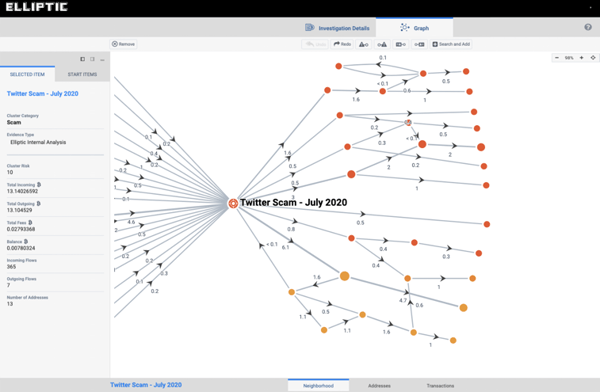
Source: Elliptical Internal Analysis (not all transaction flows shown)
A very small fraction of the funds were sent to well-known, regulated crypto exchanges (not shown in the diagram for confidentiality). This is important because it could be an important clue for law enforcement investigators looking to identify the hacker, as they can ask exchanges for the identity of the account holder who received these funds.
It is also interesting that almost half of the collected bitcoins went through a bitcoin wallet that has been active since May of this year. That wallet also had transactions with regulated crypto businesses – providing investigators with additional clues.
Helping our customers prevent laundering
The hacker is now faced with a dilemma – how to launder and cash out bitcoins, while their every move is carefully monitored on the blockchain. Exchanges using Elliptic’s software will be alerted every time a customer deposits a bitcoin resulting from this incident.
With quick action and coordination from our global team, the affected BTC and XRP addresses were immediately verified and added to our database. This allows our clients to identify, in real time, any exposure to these addresses and prevent the laundering of fraudulent proceeds through their platforms.
Although a popular payment mechanism for fraudsters, Crypto asset fund movements are in fact highly traceable via public blockchains. This inherent transparency, made systematically searchable by Elliptic’s blockchain analytics tools, enables effective anti-money laundering controls and real-time monitoring of fund flows to prevent bad actors from laundering funds. The more difficult it is for criminals to launder the proceeds of their hacks, the less likely they will be able to access and benefit from the proceeds of these criminal activities.
Related Articles:
- Elliptic Identifies Probable Use of Wasabi Wallet Service to Launder Twitter Hack Bitcoins
- Tracking Twitter Hack Bitcoins – Update from Elliptic
- Over 50% of #TwitterHack bitcoins now sent via mixer – What does this mean for crypto AML?
Don’t already have an Elliptic backup of your crypto AML compliance operations?




