Crypto lending protocol Euler Finance suffered a loss of $199 million on the morning of March 13, following an attack on Quick Loan. This figure is based on Elliptic’s analysis of on-chain transactions.
Cryptoassets taken in the hack include stablecoins USDC ($34.1 million) and Dai ($8.8 million), as well as Wrapped Bitcoin ($18.9 million) and Staked Ether ($137.1 million).
Flash loan attacks involve taking large, short-term, collateral-free crypto loans from decentralized finance (DeFi) services and using large amounts to manipulate the market and other DeFI services to their advantage.
A full analysis of the attack shows that a flaw in one of Euler Finance’s smart contracts was exploited to steal assets.
The proceeds of the attack are already being laundered through Tornado Cash, a decentralized mixer sanctioned by the US government.
The funds used to carry out the attack came from Monero wallets. Monero is an example of a type of cryptocurrency known as a “privacy coin,” which unlike Bitcoin does not have a clear public ledger of transactions.
Euler began communicating with the attacker by sending messages on the chain to the Ethereum account that has the stolen assets:
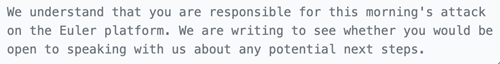
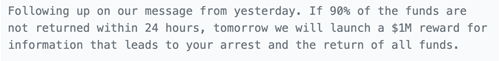
On March 17, a thief made an unusual move by sending 100 ETH to an Ethereum account linked to North Korea’s Lazarus Group. This account was used to steal funds from Ronin Bridge, in an attack attributed to Lazarus. This payment is likely a misdirection, rather than indicating that the Euler Finance hack was carried out by the Lazarus Group.
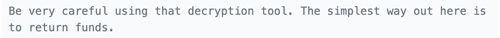
On March 21, the thief hinted that they could return the funds:
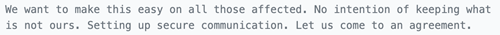
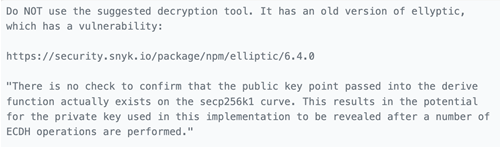
Later that day, the thief received a message from the Lazarus Group account that received 100 ETH. The message claims to include a message that has been decrypted and can only be decrypted with the Euler Finance thief’s private key. The message included a link to software that could be used to perform this decryption:
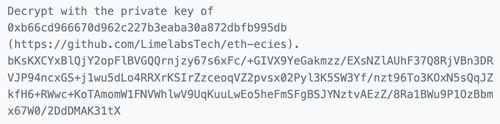
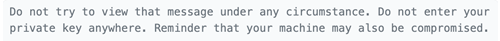
Euler himself immediately sent further messages to the thief, warning them that the Lazarus Group might be trying to trick them into revealing their private key (and therefore the stolen property), using malware:
Businesses can track funds using Elliptic’s transaction screening and investigation tools.
Legal Compliance Stablecoins



