Binance has confirmed an exploit on the Binance Smart Chain (BSC) that resulted in $569 million worth of BNB being minted.
The attacker(s) became the transmitter for Binance Bridge (BSC Token Hub) before exploiting the proof-of-verification vulnerability, allowing them to deposit two million BNB to BSC address 0x489A8756C18C0b8B24EC2a2b9FF3D4d447F79BEc.
BSC Token Hub
BSC Token Hub connects assets between BNB Beacon chain (BEP2) and BNBChain (BEP20 or BSC). The exploit resulted in a chain-wide shutdown – as Binance CEO Changpeng Zhao said explained early on October 7 – in an attempt to stop the exploiter from moving the funds any further.
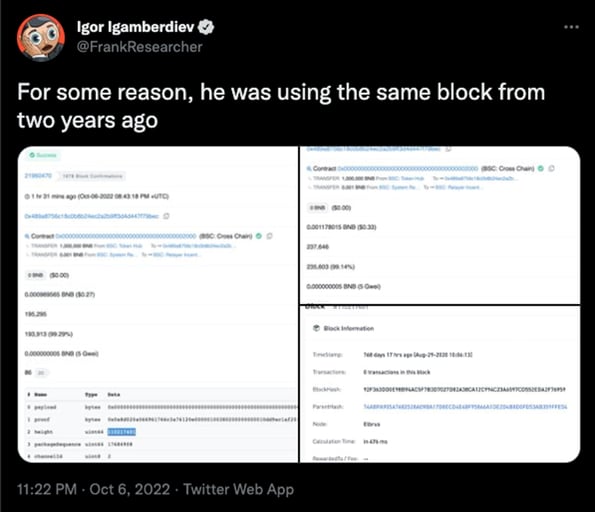
According to a Twitter user @FrankResearcherattackers managed to find a way to forge the proof of block 110217401 – the block confirmed two years ago. Based on their findings, the vulnerability was exploited by forging arbitrary messages to create new tokens.
A story about bridges, decentralized exchanges and DeFi protocols
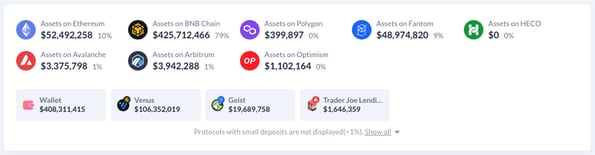
The newly created BNB tokens were then exchanged for other assets on and off the BNB smart chain, including Ethereum, Polygon, Fantom, Avalanche, Optimism and Arbitrum.
debank.com
Fortunately, the quick reaction of the community meant that most funds were quickly either frozen or made unavailable. Shortly after the attack, a total of $33.5 million worth of assets held by the exploiter were frozen by USDT and USDC issuers Tether and Circle. With this and Binance’s quick action to pause the network, over $350 million worth of cryptoassets became inaccessible to the attacker(s) after the concerted move.
At the time of writing, just over $45 million worth of funds were held in censorship-resistant cryptoassets on the Ethereum blockchain – in ETH and wETH.
Collateralized loans
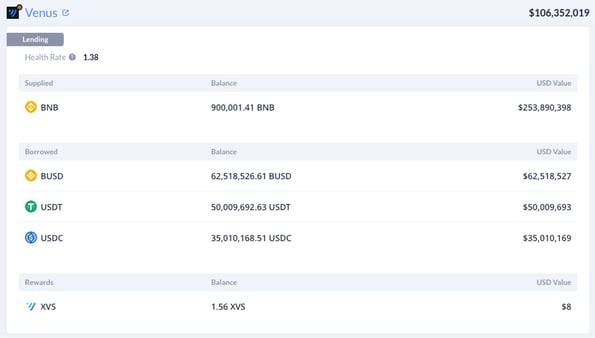
Among the various DEXs and bridges used by the hackers after the exploit, Venus Protocol (on BSC) and Banker Joe (part of Trader Joe’s in the Avalanche chain) were the two lending protocols used by the hacker to open collateralized positions. In a somewhat confusing move, 900,000 newly minted BNB and 8 million USDT were used as collateral in these lending protocols. At one point it appeared that one of these positions could be at risk of liquidation if the price of BNB fell below $220.
debank.com
The sometimes confusing movement of funds after exploitation has caught the eye of many investigators and analysts. Elliptic’s internal research – recently published in its State of Cross Crime report – found that exploiters were generally more methodical in laundering or protecting the proceeds of crime.
Criminals commonly used DEXs and bridges in the following ways:
- Token swapping to avoid asset freezes: Certain cryptoassets such as USDT and USDC may be frozen by their issuers if they are found to be held by illegal wallets. Criminals therefore use DEXs to exchange freezeable assets with non-freeze ones, such as ETH or DAI – stablecoins that cannot be frozen.
- Token exchange for ETH: usually in preparation for sending through Tornado Cash. This was a particularly prominent use case before the United States sanctioned Tornado Cash.
- Token exchange in preparation for bridging with other blockchains: For example, funds can be exchanged into renBTC – a wrapped version of BTC on Ethereum that can then be bridged to the Bitcoin blockchain using RenBridge. The Bitcoin blockchain has plenty of mixers and other obfuscation services available that may become increasingly attractive alternatives to criminals after Tornado Cash is sanctioned.
In this case, the exploiter(s) exchanged USDT and USDC, which were quickly frozen by Tether and Circle in all the chains the exploiter was using. It is unclear why the criminal did this instead of traditional methodologies. What is clear, however, is that the actions that followed the attack did not show the same level of ingenuity as the original feat, suggesting a lack of preparedness that its success may have come as a surprise.
How can Elliptic help?
Elliptic has taken immediate action to ensure that exploiter addresses are flagged and available for review within our tools. Users of our Elliptic Lens wallet verification tool and our Elliptic Navigator transaction tracker will be able to ensure that they are not processing funds stolen in this large-scale attack.
Elliptic’s new Holistic Screening tool, powered by Nexus – Elliptic’s new blockchain analysis engine – will allow compliance teams to screen crypto transactions and wallets regardless of asset or blockchain. This significantly simplifies and reduces the burden on compliance resources.
New Elliptical Report: The State of Cross Crime
As new technologies remove many barriers to the free flow of capital between cryptoassets, blockchains are becoming increasingly interconnected. However, they are also misused for money laundering by groups such as ransomware groups and hackers.
In our brand new report, we take a deep dive into the criminal exploitation of three services that can commonly be used anonymously to facilitate cross-chain activity. You can access the report here.
Crypto Crime Cross-Chain Compliance



